Active Information Gathering
by HU22CSEN0400157 : V.satvik
DNS Zone Transfer
- In certain cases DNS server admins may want to copy or transfer zone files from one DNS server to another. This process is known as a zone transfer.
- If misconfigured and left unsecured, this functionality can be abused by attackers to copy the zone file from the primary DNS server to another DNS server.
- A DNS Zone transfer can provide penetration testers with a holistic view of an organization's network layout.
- Furthermore, in certain cases, internal network addresses may be found on an organization's DNS servers.
- Tools or utilities you can use
- dig
- dnsenum
- fierce
- Usage:
dig axfr @<ns> <domain>
dnsenum <domain name>
fierce -d < domain name>
Host Discovery with nmap
- This is used to enumerate the devices connected to your local network
- we can use
nmaptool to do this by using a ping scan - usage :
nmap -sn 192.168.20.0/24 [ YOUR IP ADDRESS ]
output
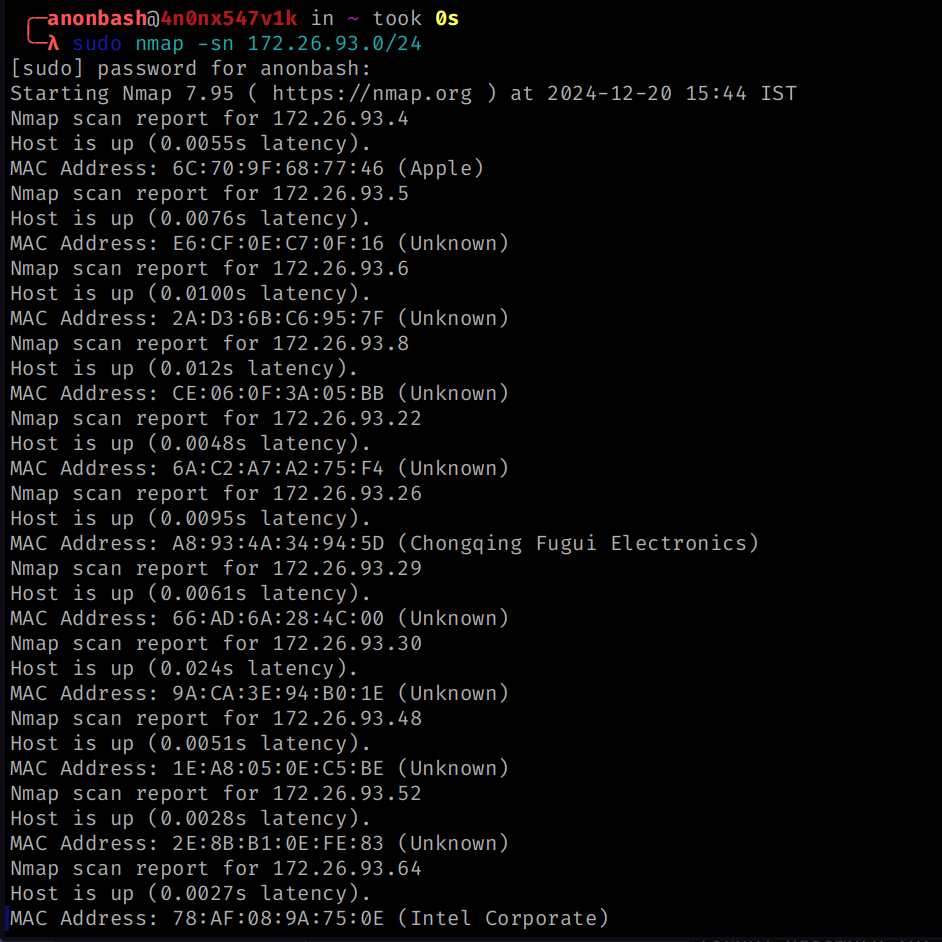
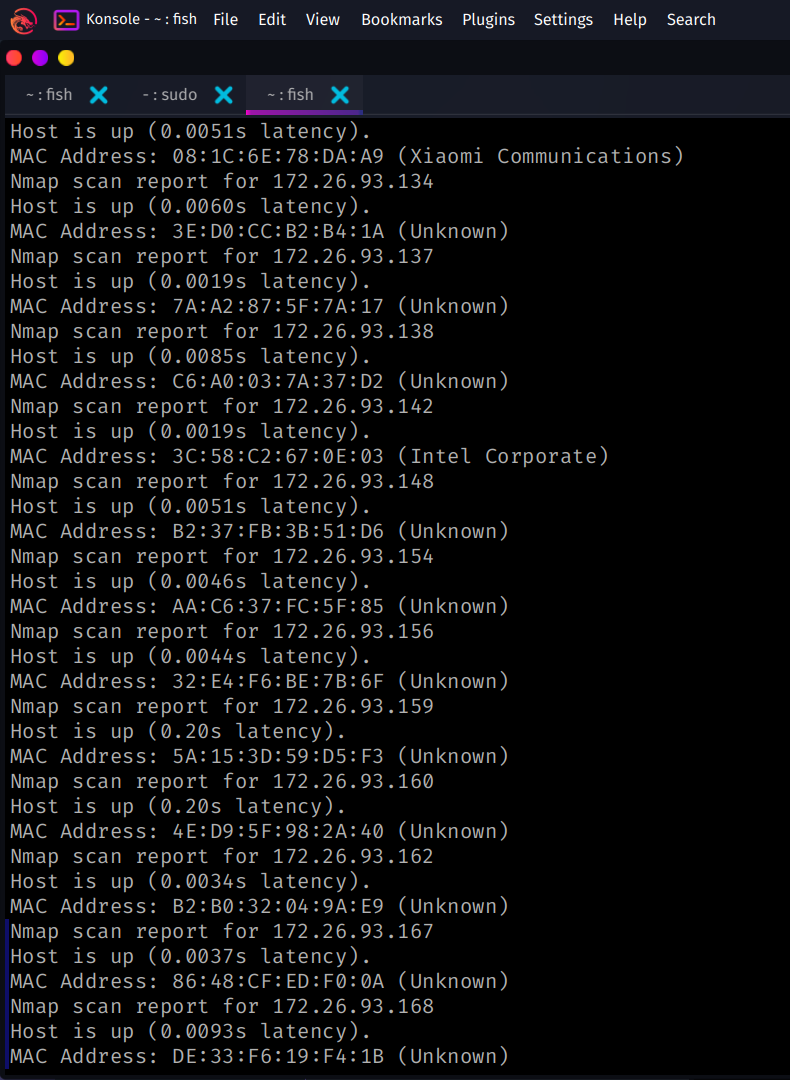
So these are all the devices in my local network
Port Scanning with nmap
We can use nmap for various scans
Port Scan:
sudo nmap -Pn 185.199.109.153
Output :
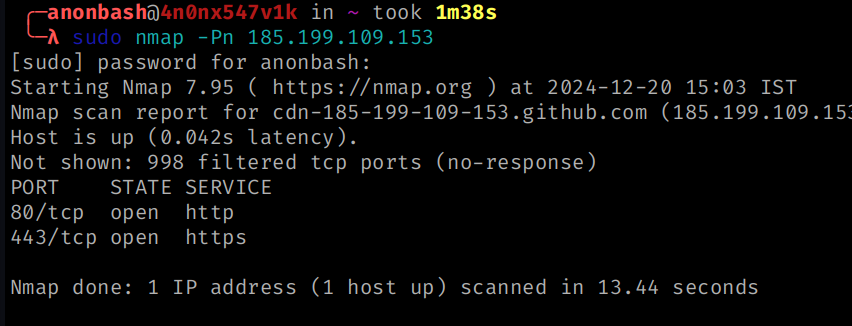
Specifying port range:
sudo nmap -p1-500 5.196.105.14 -Pn
-p- --> to scan all 65535 ports
-p80 --> to only scan port 80
-p80,445 --> to only scan port number 80 and 445
-p1-500 --. it will scan all ports between 1-500
and also perform service scan
Output :
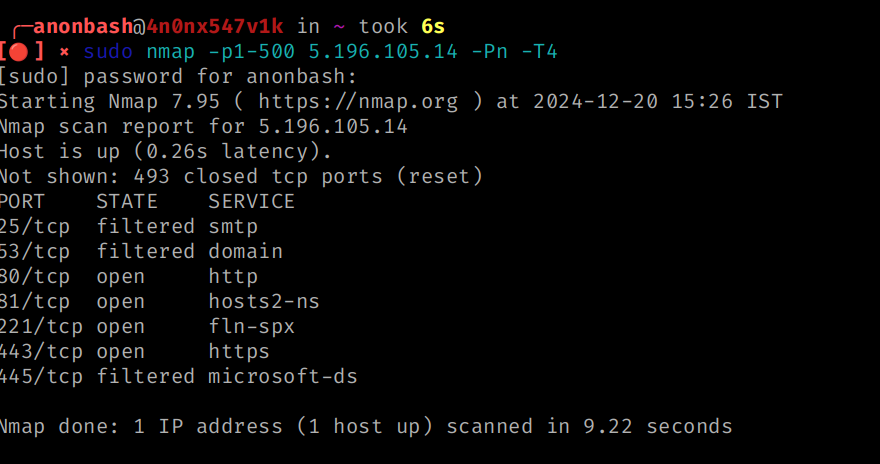
Version Scan:
sudo nmap -sV 5.196.105.14 -Pn -v
-v for verbose
-sV performs service version scan that means it will enumerate the services of that host and its versions
-Pn means it will perform ping scan so that it will treat all hosts are online and prevents blocking from the firewall
# this scan will basically give you the information regarding the versions of the particular Services
Output :
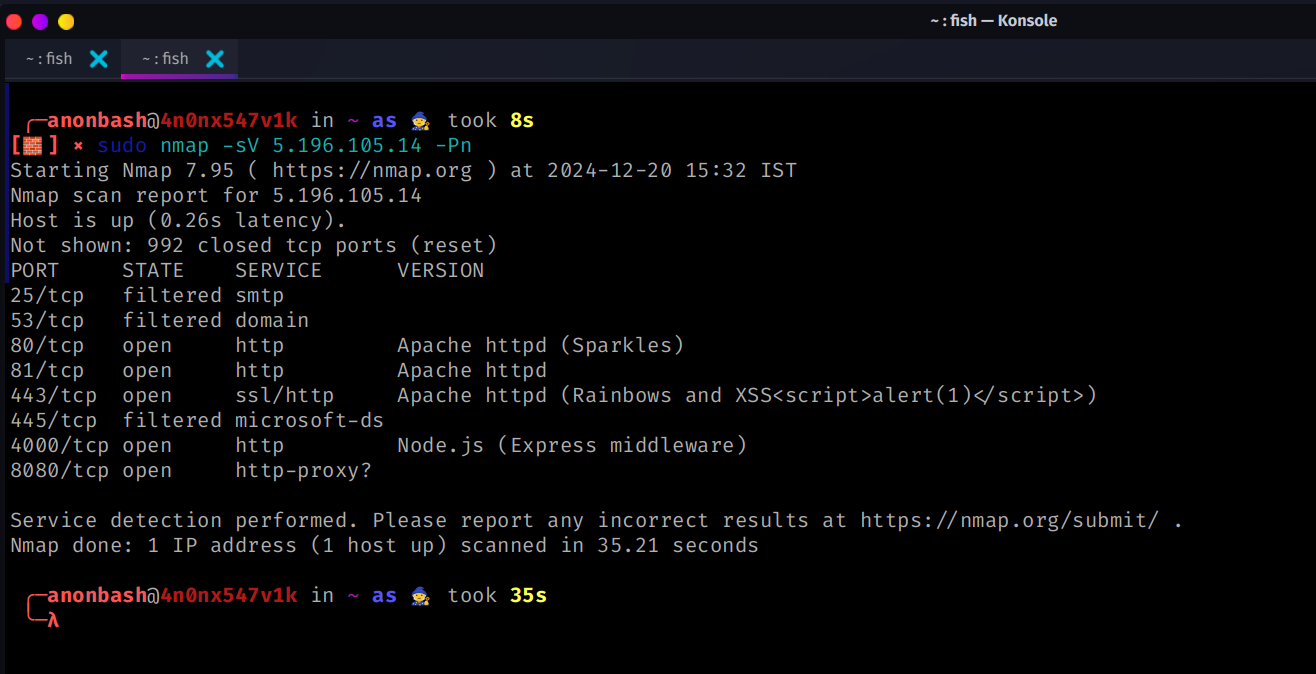
OS Detection:
sudo nmap -O 5.196.105.14 -Pn
-O - This detects the OS of that particular service
-Pn means it will perform ping scan so that it will treat all hosts are online and prevents blocking from the firewall
Output :
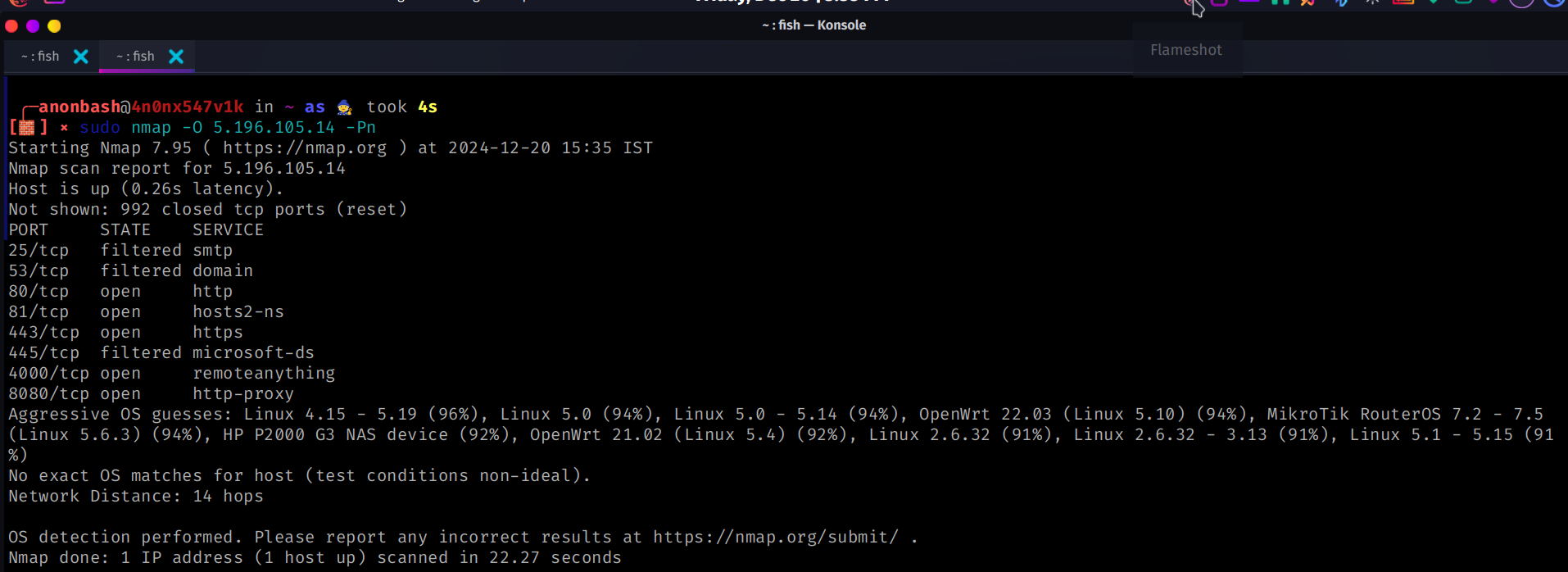
Verbose / Limiting the speed of the scan:
sudo nmap -sV -T4 -v 5.196.105.14 -Pn
-T4 : it is the speed limit of the scan ; T3 < T4 < T5
-v : will give you the real time scan report on the screen
Output :
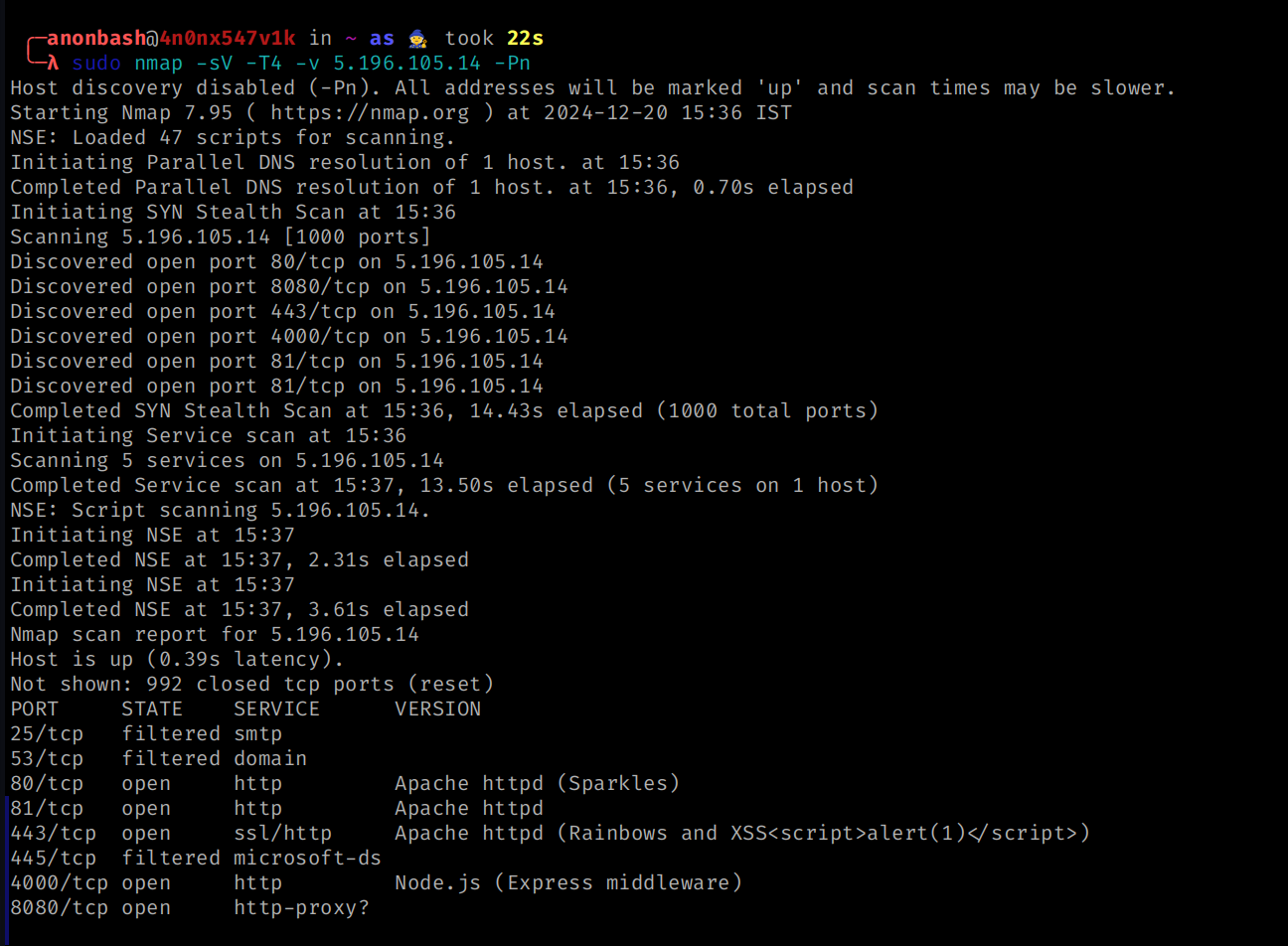
So it gives real time data while scanning
**Aggresive OS Detection for Accurate details of Operating system :
nmap -sS -O --osscan-guess -p- 5.196.105.14
-sS performs SYN scan
--osscan-guess performs OS Detection on the site
-p- performs port scan against all ports ( 65535 )
This scan takes hours to execute
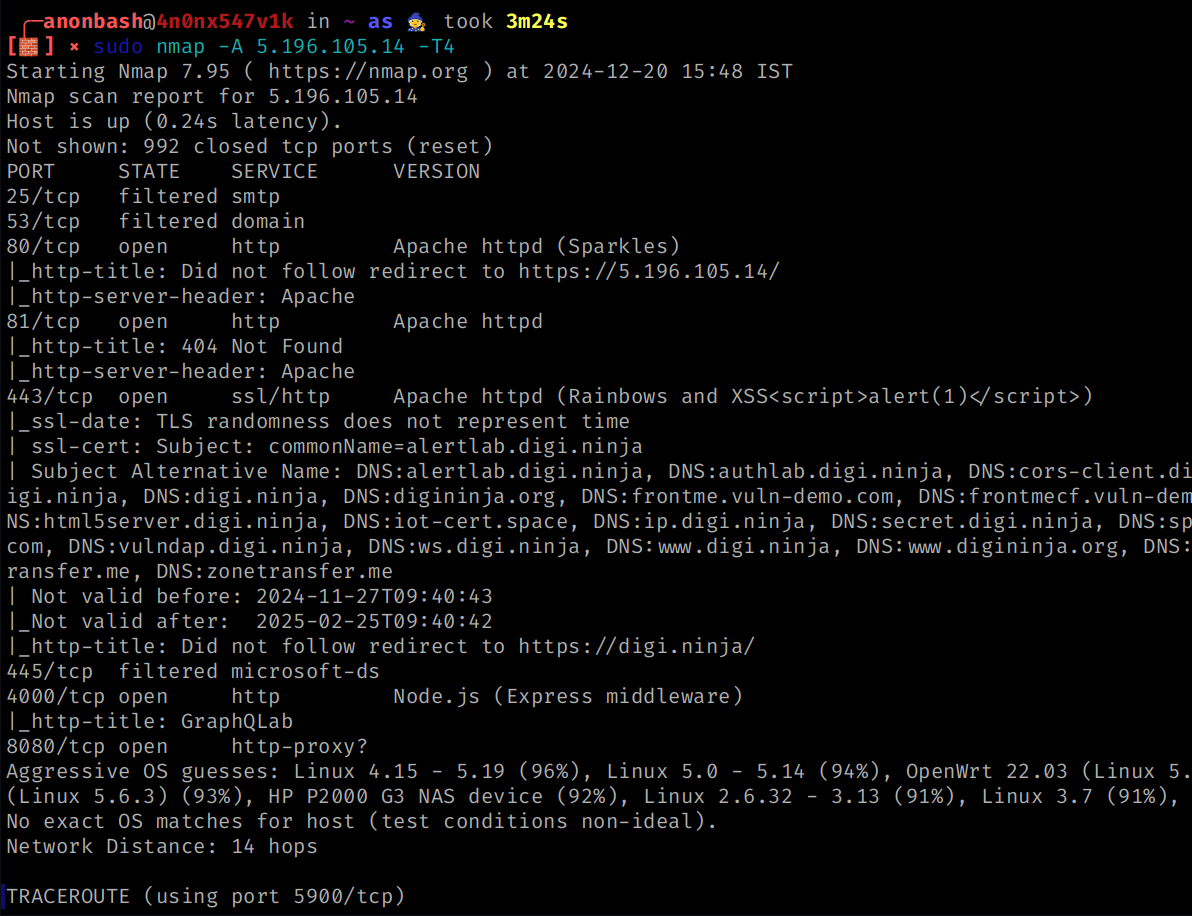
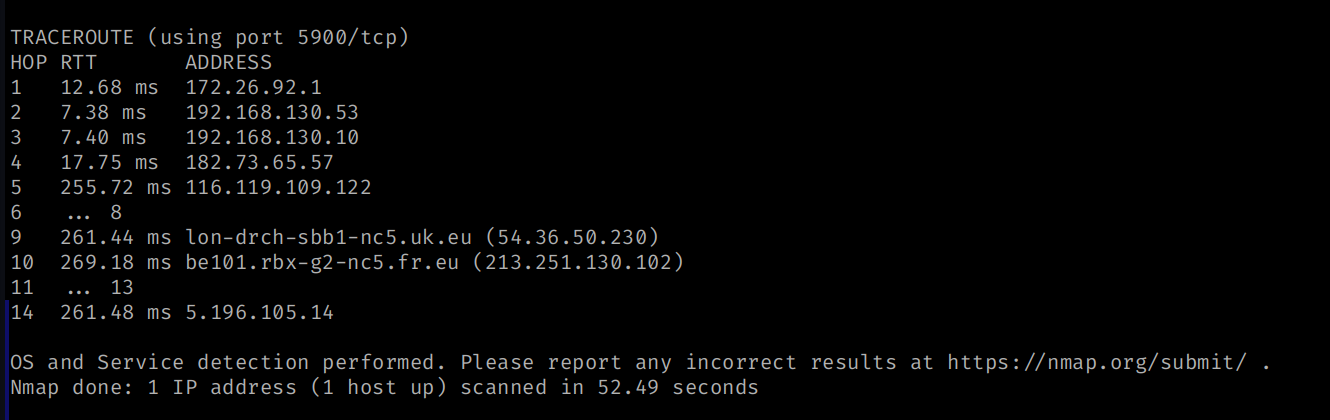
Aggressive Scan
sudo nmap -A 192.168.9.2 -Pn -T4
-A : This agressive scan will combine the Script , OS , Version scans
-A = -sC , -sV , -O
-Pn it will perform ping scan to evade from firewalls
-T4 = Template 4 means it will speed of the scan
output :
HOME : Satvik's Hacking Garden